Development of Attack-Resilient Cyber-Physical Systems
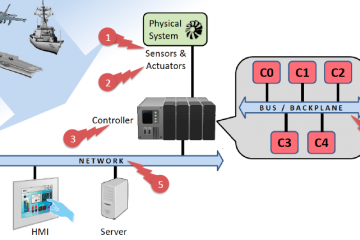
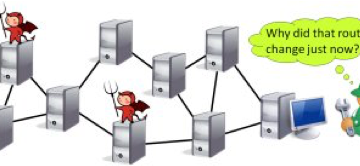
The project aims to develop control systems for ground vehicles that are resilient to a variety of external attacks. Our approach is to combine control-level techniques and code-level techniques, resulting in the approach comprises of two major stages: control law design and control task synthesis. Control-level defenses address attacks on Read more…