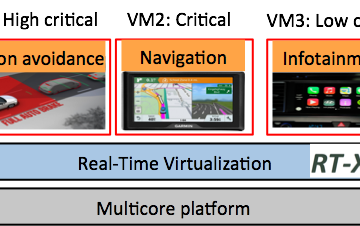
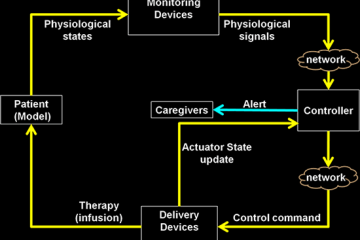
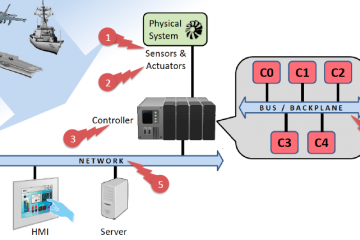
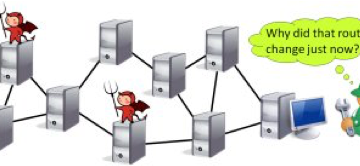
Mathematical Limits of Lattices in Cryptography
Nearly all of public-key cryptography relies on the assumed difficulty of solving various number-theoretic problems. Recent spectacular developments in cryptography such as fully homomorphic encryption, candidate multilinear maps, and efficient post-quantum lattice-based cryptography have produced a multitude of new algebraic and number-theoretic cryptographic hardness assumptions. Many of these problems are Read more…