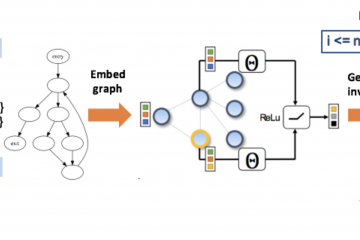
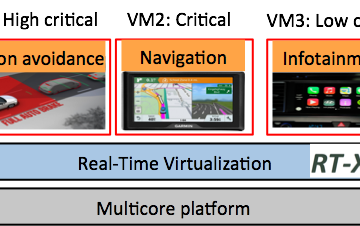
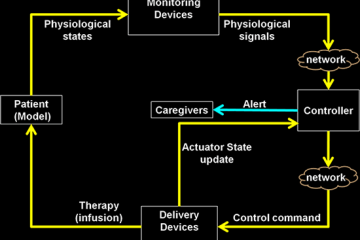
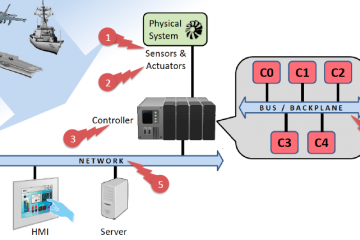
Modern Machine Learning Algorithms for Ranking and Choice Data
Problems involving learning from ranking and choice data arise in several domains, ranging from sports rankings to elections and from recommender systems to marketing. Indeed, algorithms for these problems have been developed in many different fields, ranging from statistics to computer science and from social choice to marketing. Unfortunately, however, Read more…